Authored by Fernando Ruiz
The popularity of AI-based mobile applications that can create artistic images based on pictures, such as the “Magic Avatars” from Lensa, and the OpenAI service DALL-E 2 that generates them from text, have increased the mainstream interest of these tools. Users should be aware of those seeking to take advantage to distribute Potential Unwanted Programs (PUPs) or malware, such as through deceptive applications that promise the same or similar advanced features but are just basic image editors or otherwise repackaged apps that can drain your data plan and battery life with Clicker and HiddenAds behaviors, subscribe you to expensive services that provide little or no value over alternatives (Fleeceware), or even steal your social media account credentials (FaceStealer).

Dozens of apps surface daily claiming to offer AI image creation. Some of them might be legitimate or based on open-source projects such as Stable Diffusion, but in the search for a free application that produces quality results, users might try new apps that could compromise their privacy, user experience, wallet and/or security.
The McAfee Mobile Research Team recently discovered a series of repackaged image editors on the Google Play app store which presented concerning behaviors. McAfee Mobile Security products help protect against such apps, including those classified as Android/FakeApp, Android/FaceStealer, Android/PUP.Repacked and Android/PUP.GenericAdware.
McAfee, a member of the App Defense Alliance focused on protecting users by preventing threats from reaching their devices and improving app quality across the ecosystem, reported the discovered apps to Google, which took prompt action and the apps are no longer available on Google Play.
We now discuss various types of privacy and/or security risks associated with the types of apps recently removed from the app store.
FaceStealer
“Pista – Cartoon Photo Effect” and “NewProfilePicture” are examples of apps that offered compelling visual results, however, each was based on the same image editor with basic filters and trojanized with Android/FaceStealer, which is a well-known malware capable of compromising a victim’s Facebook or Instagram account. The apps could capture user credentials during a Facebook login by embedding a javascript function loaded from a remote server (to evade detection) into a flutter webview activity that displays the Facebook login screen.
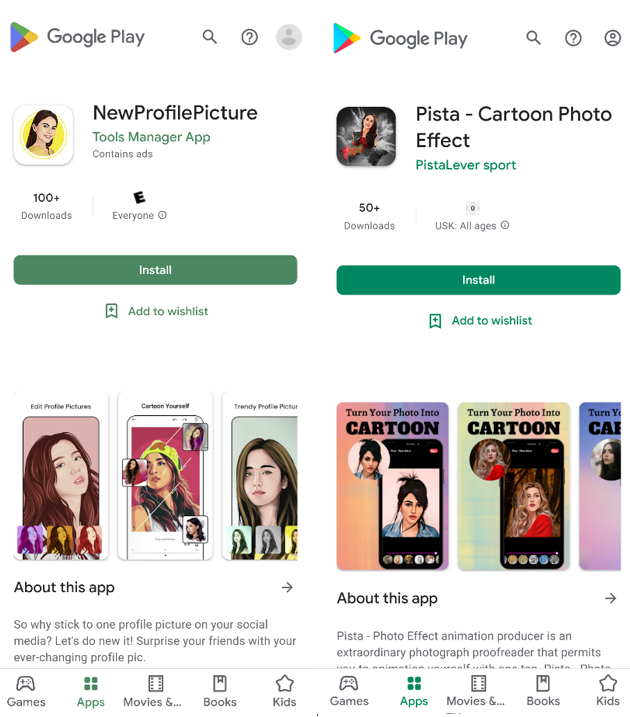
“NewProfilePicture” and “Pista – Cartoon Photo Effect” are examples of FaceStealer malware that posed as a cartoon avatar creator.
The same image editor which was repackaged into the above two apps has also been repackaged alternatively with adware modules and distributed by other developers under other app names, such as “Cartoon Effect | Cartoon Photo”:
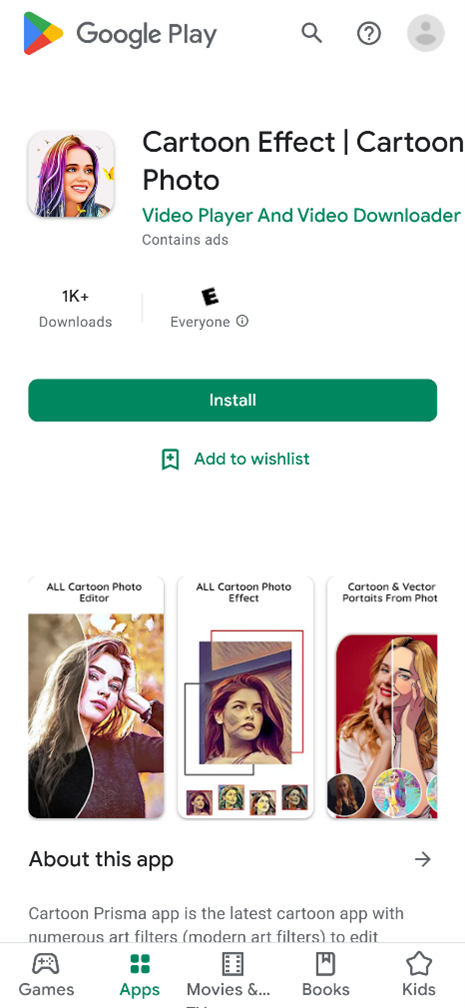
Fleeceware
Fleeceware refers to mobile apps that use various tactics to enroll users into subscriptions with high fees, typically after a free trial period, and often with little or no value to the subscriber beyond cheaper or free alternatives. If the user does not take care to cancel their subscription, they continue to be charged even after deleting the app.
“Toonify Me”, which is no longer available on the Play Store, cost $49.99 per week after 3 days – almost $2,600 per year – for what featured AI-generated illustrations in the app description, but was another repackaged version of the same image editor functionality found within “NewProfilePicture” and “Pista – Cartoon Photo Effect”.
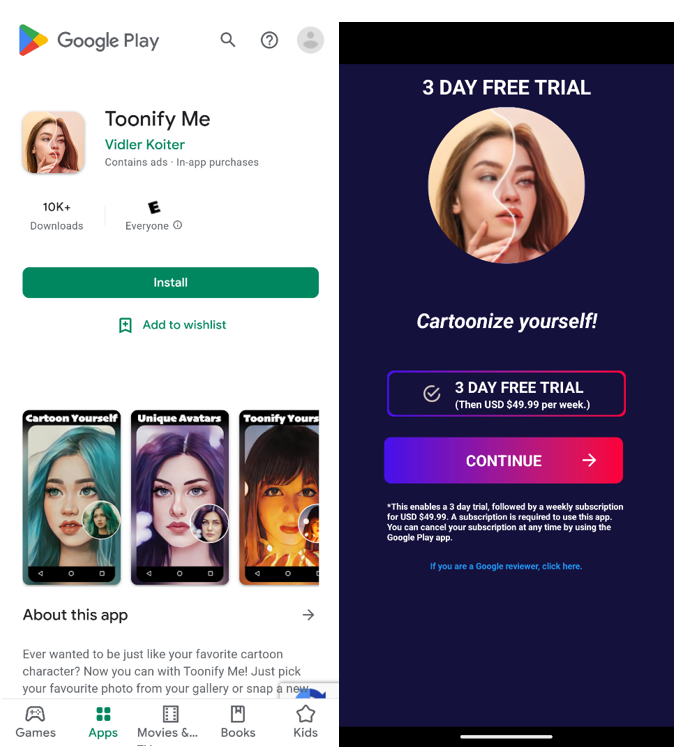
In this case, the “Toonify Me” app did not allow feature access without enrolling in the subscription, and the “CONTINUE” button which initiated the subscription was the only option to tap in the app once it was launched.
Adware
Promoted by ads that described it as capable of transforming pictures into artistic drawings, the “Fun Coloring – Paint by Number” app is an example of a repackaged version of a different, legitimate pixel painting app. It lacked the advertised AI effects and was plagued with adware-like behavior.

Advertisement of “Fun Coloring – Paint by Number” on social media which included app store link
Consistent with many reviews complaining about unexpected ads out of the context of the app, once installed, the app started a service that communicated in the background with Facebook Graph API every 5 seconds and might pull ads based on received commands after some time of execution. The app contained multiple injected SDK modules from AppsFlyer, Fyber, InMobi, IAB, Mintegral, PubNative and Smaato (none of which are in the original app, which was repackaged to include these), which would help monetize installations without regard for user experience.
Conclusion
When new types of apps become popular and new ones appear on the market to offer similar features, users should act with caution to avoid becoming victim to those wanting to exploit public interest.
When installing an app that causes you doubt, make sure you:
- Read the pricing and other terms carefully
- Check those permissions requested are reasonable with the purpose of the app
- Look for consistently bad reviews describing unexpected or unwanted app behavior
- Verify if the developer has other apps available and their reviews
- Consider skipping the app download if you aren’t convinced of its safety
Even if an app is legitimate, we also encourage users to look closely before installation at any available privacy policy to understand how personal data will be treated. Your face is a biometric identifier that’s not easy to change, and multiple pictures might be needed (and stored) to create your model.
Artificial intelligence tools will continue to amaze us with their capabilities and probably will become more accessible and safer to use over time. For now, keep in mind that AI technology is still limited and experimental, and can be expensive to use – always consider any hidden costs. AI also will bring more challenges as we discussed on the 2023 McAfee Threat Prediction blog.
IDENTIFIED APPS
The following table lists the application package name, hash sum SHA256, the minimum number of installations on Google Play, and the type of detected threat. These apps were removed from Google Play, but some may remain available elsewhere.
| Package Name | SHA256 | Installs | Type |
| com.ayogamez.sketchcartoon | 9cb1d996643fbec26bb9878939735221dfbf639075ceea3abdb94e0982c494c1 | 5M | Adware |
| com.rocketboosterapps.toonifyme | 3f45a38b103e1812146df8ce179182f54c4a0191e19560fcbd77240cbc39886b | 10K | Fleeceware |
| com.nhatanhstudio.cartoon.photoeffect | 2c7f4fc403d1449b70218624d8a409497bf4694493c7f4c06cd8ccecff21799a | 5K | Repackaged Adware |
| com.cambe.PhotoCartoon | 5327f415d0e9b21523f64403ec231e1fd0279c48b41f023160cd1d70dd733dbf | 10K | Repackaged Adware |
| com.chiroh.cartoon.prismaeffect | 18fef9f92639e31dd6566854feb30e1e4333b971b05ae9aba93ac0aa395c955b | 1K | Repackaged Adware |
| cartoon.photo.effect.editor.cartoon.maker.online. caricature.appanime.convert.photo.intocartoon |
3b941b7005572760b95239d73b8a8bbfdb81d26d405941171328daa8f3c01183 | 50 | Repackaged Adware |
| com.waxwell.saunders.pistaphotoeditor | 489d4aaec3bc694ddd124ab8b4f0b7621a51aad13598fd39cd5c3d2067b950e5 | 50 | FaceStealer |
| com.ashtoon.tooncool.skordoi | 980c090c01bef890ef74bd93e181d67a5c6cd1b091573eaaf2e1988756aacd50 | 100K | FaceStealer |
| com.faceart.savetoon.cartoonedit | 55ffc2e392280e8967de0857b02946094268588209963c6146dad01ae537daca | 100 | FaceStealer |
| com.okenyo.creatkartoon.studio | e696d7304e5f56d7125dd54c853ff35a394a4175fcaf7785d332404e161d6deb | 500K | FaceStealer |
| com.onlansuyanto.editor.bading | 59f9630c2ebe4896f585ec7722c43bb54c926e3e915dcfa4ff807bea444dc07b | 10K | FaceStealer |
| com.madtoon.aicartoon.kiroah | c29adfade300dde5e9c31b23d35a6792ed4a7ad8394d37b69b5cecc931a7ad9f | 100K | FaceStealer |
| com.acetoon.studio.facephoto | 24cf7fcaefe98bc9db34f551d11906d3f1349a5b60adf5fa37f15a872b61ee95 | 100K | FaceStealer |
| com.funcolornext.beautyfungoodcolor | b2cfa8b2eccecdcb06293512df0db463850704383f920e5782ee6c5347edc6f5 | 100K | Repackaged Adware |













